My dear Livewire believers, I need your help. Yesterday, one of my projects was attacked by what I believe were automated bots.
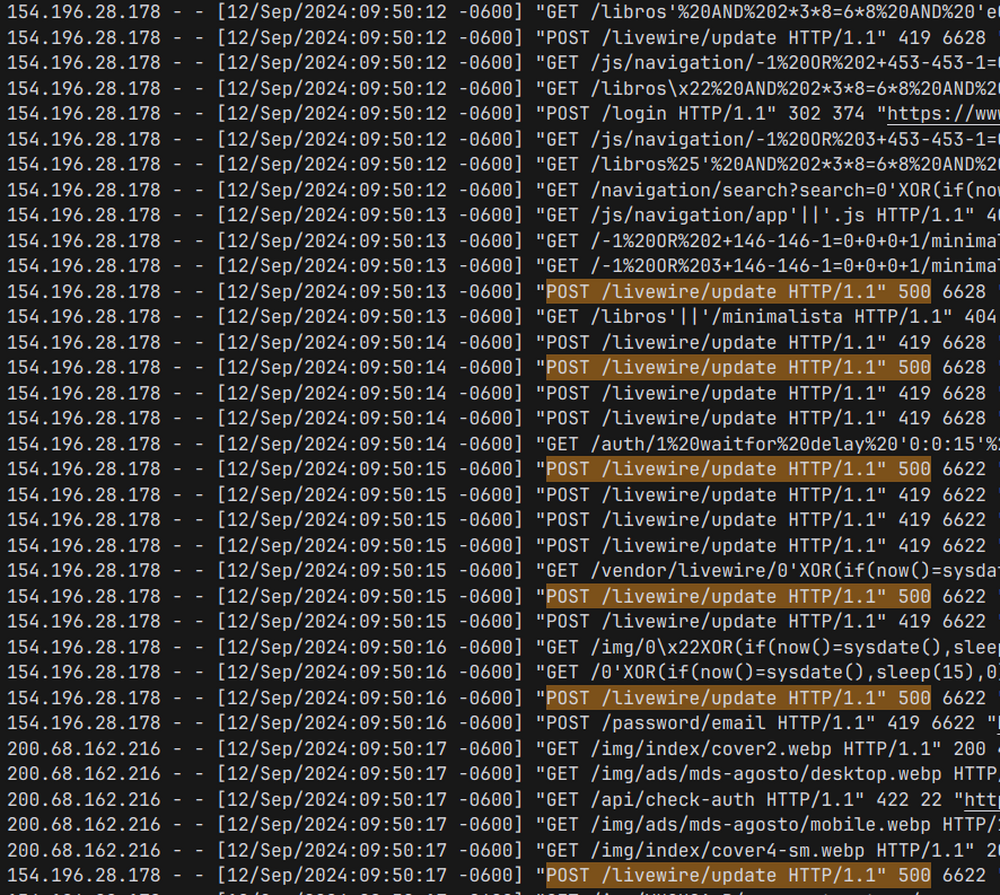
The issue is that the scripts were targeting (among other things) the "livewire/update" route. They were attempting to call methods that clearly don't exist or trying to access properties.
I suspect they might have bypassed the checksum check, but I'm not sure.
Has anyone seen anything like this before?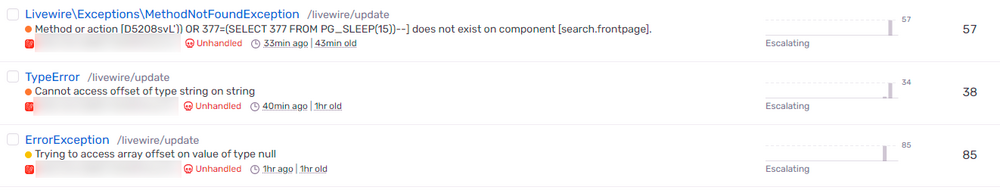
Btw it is totally possible
Even I can copy component id from snapshot and call any method or property I want with using.
Livewire.find('componentId').call('method', { parameters });Always Authorize and use #[Locked] where needed.
Don't trust on user like me 😅
Thank you Punyapal. The thing is… can you target livewire/update being a post route overriding cors middleware and livewire’s internal checksum check?
I mean they were using a Guzzle client targeting the route directly.
If so, then the route should be auth protected meaning you couldn’t use livewire component in a public page.
Also that using livewire is a big liability.
That doesn't seem posible (bypassing checksum).
Brw you can use Livewire component anywhere just be careful of sensitive data. And use it wise as much as possible 🙌

