My dear Livewire believers, I need your help. Yesterday, one of my projects was attacked by what I believe were automated bots.
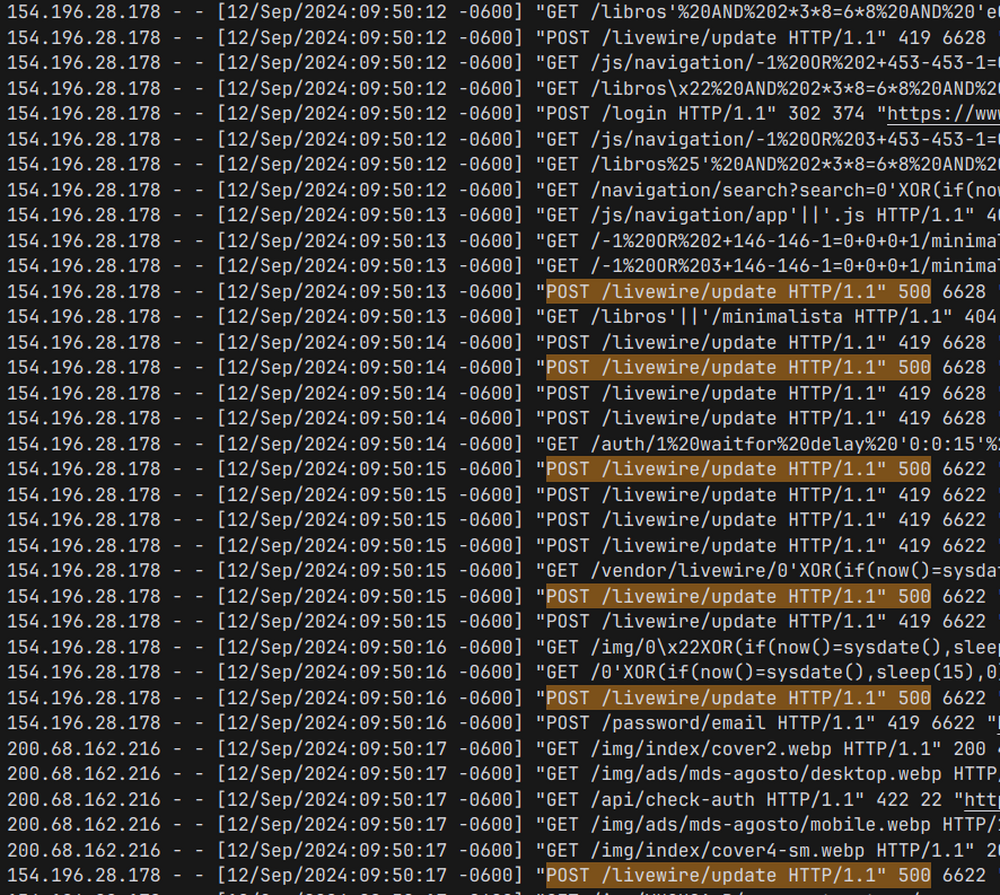
The issue is that the scripts were targeting (among other things) the "livewire/update" route. They were attempting to call methods that clearly don't exist or trying to access properties.
I suspect they might have bypassed the checksum check, but I'm not sure.
Has anyone seen anything like this before?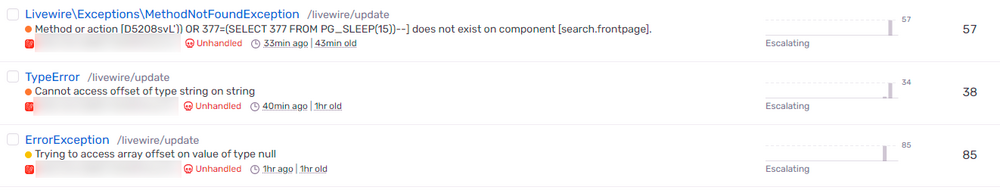
if you're behind something like cloudflare can you activate the antibot feature so you temporary block them?
Thank you Andrei. Yes it can be made with cloudflare. But what I do is that I go deep into nginx access log, copy the offending IPs and block them via firewall and also a silly global middleware that checks IPs and if in my list, they get redirected anywhere else.
I also checked in an IP address lookup service and all offending IPs are from datacenters in Belgium, Germany, Finland, SFO... so definitely automated and as far as I'm concerned, blocked forever 😂
Never heard of it, maybe they found some vulnerabilities on livewire apps? But i don't know what could it be
Btw it is totally possible
Even I can copy component id from snapshot and call any method or property I want with using.
Livewire.find('componentId').call('method', { parameters });Always Authorize and use #[Locked] where needed.
Don't trust on user like me 😅
Thank you Punyapal. The thing is… can you target livewire/update being a post route overriding cors middleware and livewire’s internal checksum check?
I mean they were using a Guzzle client targeting the route directly.
If so, then the route should be auth protected meaning you couldn’t use livewire component in a public page.
Also that using livewire is a big liability.
That doesn't seem posible (bypassing checksum).
Brw you can use Livewire component anywhere just be careful of sensitive data. And use it wise as much as possible 🙌



